Using SSL Certificates (HTTPS) with RLM
Overview
Starting with RLM version 15.1, License Administrators are now able to run the RLM web server with SSL certificates. When setup to use SSL certificates RLM’s web server will run with the HTTPS protocol.
RLM does not come with pre-configured SSL certificates. You will either need to procure your own certificates from a Certificate Authority (CA) or generate your own self-signed certificates.
Implementation
You can instruct RLM to use HTTPS during startup with the command parameters “-sslcert” and “-sslpriv”. For example:
rlm -sslcert /path/to/cert.pem -sslpriv /path/to/privkey.pem
Please note that certificate files cannot be used if they are password protected.
When launched with SSL certificates, RLM will automatically switch from listening for http requests to https requests. You will need to navigate to RLM using https:// in your URL, in v15.1 RLM will not automatically update HTTP requests to HTTPS requests. Alternatively, you can bind the RLM web administration port to port 443 (using the –ws flag during service installation), and your browser will automatically make an HTTPS call to the server’s URL.
Please note that running on any port below 1024 will require RLM to be run by an administrator.
FAQ
What Are SSL Certificates
SSL certificates are a mechanism for your web browser to verify the identity of a web server, to make sure that the traffic is coming from a known source and not a malicious third party. The web server will present to your browser information signed by the server’s private key, which the web browser will then verify using the public key on the website. The server and the browser will then agree upon a traffic encryption method, the initial identity verification is what the SSL certificates are used for.
How does a browser know to trust an SSL certificate?
SSL public keys can be signed by a Certificate Authority (CA) to create a certificate hierarchy for an SSL certificate. Operating Systems (OS) and Web Browsers contain a built-in library of “root certificates” created by CAs that are known to be trusted. Your OS or browser will then review a website’s certificate hierarchy until it finds a root certificate that is trusted.
You can view this certificate hierarchy in most web browsers. For Google Chrome you can click on the padlock symbol in the address bar -> Connection is secure -> Certificate is valid -> Details

How do I get an SSL Certificate
There are many ways to create or procure SSL certificates for your web site. A few options are listed here:
Purchase
You can purchase SSL certificates from certificate providers. These certificates are usually sold in units of years (a 1-year certificate, a 5-year certificate, etc.), with longer certificates usually costing more. These companies will require you to verify your identity in some way.
In general, purchased certificates are trusted more by OS and browsers.
Free Services
Free services such as Let’s Encrypt will provide SSL certificates for you. These services usually require you to verify ownership of both your domain name and the server, ex: making modifications to your domain’s DNS. These certificates are usually issued for a few months at a time, meaning you’ll either have to manually renew frequently, or automate the process.
In general, free certificates are trusted by most OS and browsers. Older computers or locked down systems may reject these certificates.
Create your own
You can create/generate your own SSL certificates. These certificates will not be signed by a CA and so most web browsers will display a warning message to your users.
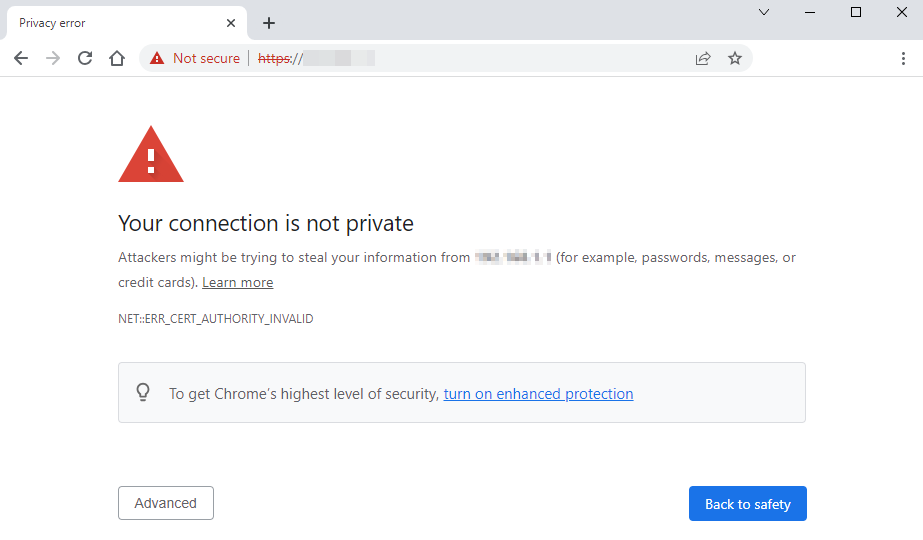
In general, self-created certificates (sometimes called self-signed certificates) are not trusted by OS or browsers. You can add your own certificate to your devices’ certificate store, but other devices connecting to your server will not have the certificate and display a warning message.
Some organizations have internal CAs where a certificate can be added for all devices belonging to that organization.
I am unable to connect to the Web Server after implementing SSL certificates
Make sure you’re connecting to your RLM server via HTTPS, as HTTP requests will not be redirected automatically. Your URL should look like:
- https://hostname:[port-number] or
- https://ip-address:[port-number]
When using 443 for the web administration port, no port is needed on the URL.
My browser says the site is insecure
Most likely this is because you are using a self-signed certificate that isn’t trusted by your OS or browser. It’s also possible that your certificate has expired, or you are accessing the site before the start date in the certificate.

